For businesses; cybersecurity risk can range from risks that are of relatively low concern; such as software that needs to be updated; all the way to major hazards like sophisticated cyber attacks.
A 2022 survey by the Office for National Statistics found that 39% of UK businesses had identified a cyber attack; and 31% of those businesses estimated they were attacked at least once a week. In the current cyber landscape; putting risk management processes in place – and reviewing their effectiveness – is key.
What does cybersecurity risk management look like?
Managing risk is a vital part of any cybersecurity framework. The risk management process is as much about mitigating the impact of a risk as it is about preventing that risk occurring; and can be split into four key areas:
- Identifying the risk
- Analysing the potential impact
- Treating the risk
- Evaluating the treated risk
Identifying the risk
To start identifying risks; use your organisation’s asset register. This is a list of information assets and elements such as your company’s hardware; software; information and infrastructure; as well as physical assets like office buildings and employee laptops.
Focus on each asset and consider what could pose a potential risk to that asset. For example; if you use an external HR system; one associated risk would be your company’s HR files being lost; stolen or negatively impacted. One risk associated with a staff member’s laptop would be a human error mistake; such as clicking on a phishing link in an email.
Once you have identified potential risks; you can begin to analyse the impact of those risks on your organisation.
Analysing the potential impact
At Hicomply; we use an ISO 27001 risk assessment methodology evaluate a risk and its impact. The matrix we use scores the likelihood of a risk occurring and the impact should the risk occur; both from 1-5.
For example; a risk like an external HR system losing your files may be considered likely (4) and would have a major impact (4). Calculate the risk score by multiplying the numbers together – in this case; the risk would be classed as 16 or ‘intolerable’.
The risk matrix below shows a risk assessment with a set of initial risk scores. The numbers in each box represent the number of identified risks in each category.
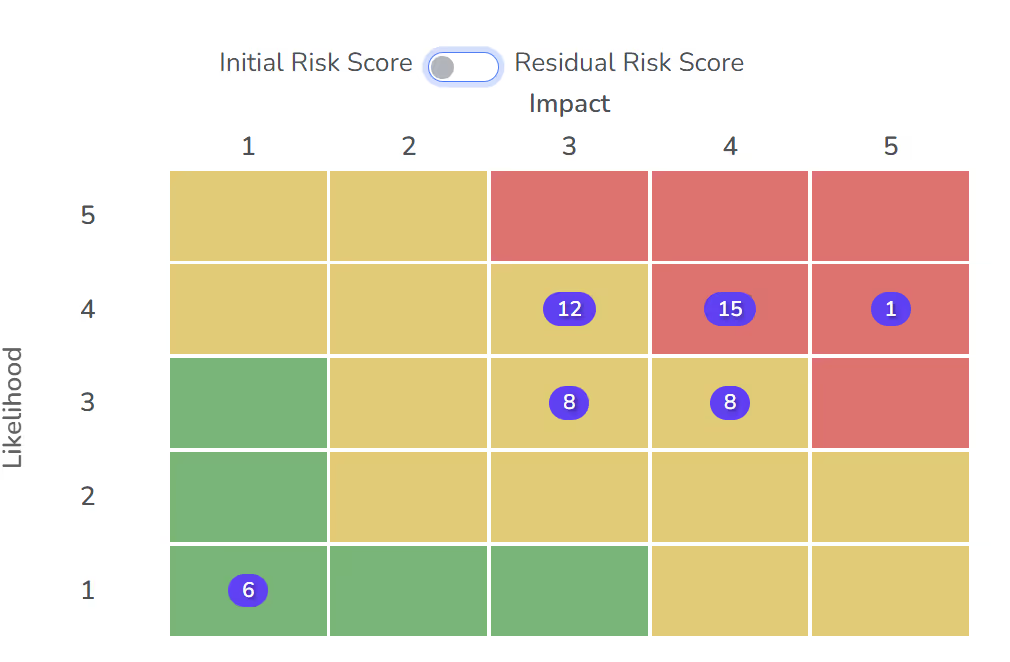
As well as scoring the risk against the assessment matrix; you should also consider the impact on your information’s confidentiality; integrity and availability. In the example used:
- Significant amounts of sensitive information or even some highly sensitive information could be exposed; risking confidentiality
- Some business critical information could be partly corrupted or destroyed; making integrity a concern
- Critical business services may be interrupted intermittently; compromising availability.
Mitigating the risk
Once you have identified the risks associated with your asset register; the next step is to consider how to manage them.
Option 1: Treat the risk
Treating risk is usually done by implementing security controls; such as those required by information security standards like SOC 2 and ISO 27001.
For example; the risk of information leakage or disposal associated with a staff member’s laptop may be treated by:
- Successfully complying with Cyber Essentials Plus; which covers the use of laptops and mobile devices
- Implementing an acceptable use policy
- Ensuring your employees undertake specific training
- Implementing a well-designed bring your own device policy.
Option 2: Tolerate the risk
You may find some risks that fall within an acceptable range or fit acceptable criteria outlined by your organisation and choose to tolerate them. For example; your organisation may decide that a risk score of 10 is the highest tolerable risk and the level of risk you are willing to accept; so any risk with the score of 10 or below can be tolerated and monitored.
Option 3: Transfer the risk
Transferring risk is the act of choosing to share the risk with a third party; for example by taking out insurance. This means that the risk responsibility is taken on by the third party.
Option 4: Terminate the risk
Terminating the risk is the act of ending the activity causing the risk. Your organisation may choose to remove the assets or processes causing the risk.
Evaluating the treated risk
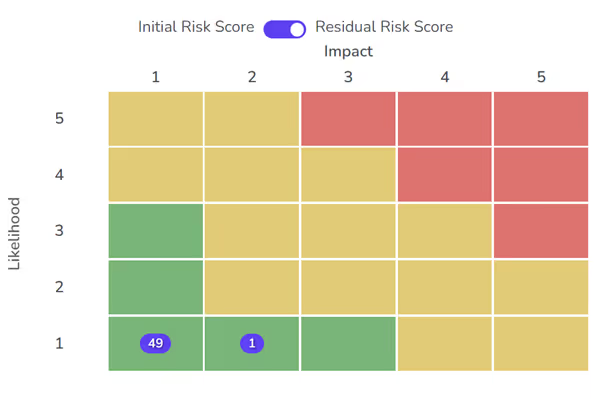
Once you have treated the risks you’ve identified; you’ll be able to calculate each risk’s residual score. Below is the same risk assessment matrix previously shown; showing risk scores after treatment; tolerance; transfer or termination.
Further reading
- Learn more about the Hicomply platform's risk management solution
- Discover six steps to ISO 27001 certification success
- Is user error the biggest risk to your organisation?





.svg)




