ISO 27001 Certification: Six Steps To Success
Researching how to get ISO 27001 certification for your business can be an intimidating task, entailing a huge amount of research and information. You know that ISO 27001 implementation will help your business achieve and maintain critical security standards and win new clients, but where do you start? In this blog post, we’ve put together our six step guide to help you achieve ISO 27001 certification success within the Hicomply platform.

Step One: ISMS Scope
Defining the scope of your information security management system (ISMS) allows you to ensure that your ISMS suits your business. This scope should take into account your company size, complexity, legal and regulatory requirements and any external and internal issues.
By defining the scope of your ISMS, you define the information your business intends to protect, whether this is on premise, in the cloud, remotely accessible or on a network. This should include all your company’s systems, processes, locations and products or services that need to be protected. When you’re being audited for ISO 27001 certification, your auditor will check that the elements of your ISMS work within your scope.
For many businesses, scoping an ISMS often means management must undertake an in-depth process involving gathering information from both inside and outside the business. Hicomply’s solution, however, distils the ISMS scoping process into an intelligent data collection procedure for ease, speed and consistency.
Step Two: Create Your Asset Register
Once you have defined the elements that sit within your ISMS scope, the next step is to pull together your business’s asset register. In the context of ISO 27001, assets include elements such as the company’s hardware, software, information and infrastructure. The purpose of your asset register is to record and manage your assets.
ISO/IEC 27001:2013 Annex A.8.1.1. states: “An inventory of all the assets associated with information and information facilities in your organisation must be recorded. The assets should be considered throughout their life cycle. […] Ensure that your inventory is well labelled, updated, free of errors and compliant with other records available.”
Example ISO 27001 Compliant Asset Register
In the example asset register above, assets are recorded by name, type, location and ownership, making them easy to identify and, further, assess the risk to each type of asset in step three. Asset types include physical systems, software, removable media and more. It’s helpful to include this information when building your asset register so that your auditor can easily check.
If you’re unsure where to start with your asset register, discover how Hicomply allows you to quickly and easily generate and manage your asset inventory.
Step Three: Start Your Risk Assessment And Set Up Key Tasks
Once you’ve pulled together your asset register, the next step is to evaluate the risks to those organisational assets. This process ensures that you understand how risks could impact your business and have a plan in place to mitigate these risks.
One approach is to consider the likelihood of each risk scenario and the impact – how much damage this could cause. This will allow you to develop a risk score, as visualised on the matrix below:
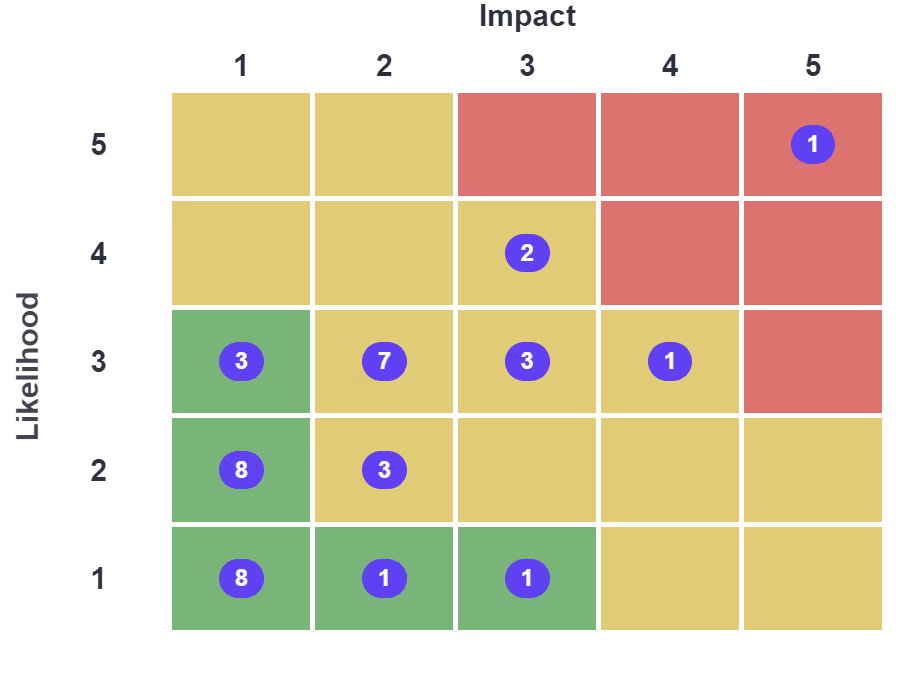
Example ISO 27001 Risk Assessment Matrix
You should then set up actions to manage and reduce risks depending on which category they fall into. This could be by applying security controls, for example the controls from Annex A, to decrease risks, such as controls for the management of access rights of users or controls relating to network security.
ISO 27001 Implementation: Risk Assessment And Mitigation Example
Malware or hacking attacks could be considered a risk to shared desktop computers. To mitigate this risk, your business could implement detection, prevention and recovery controls to protect against malware and you could combine this with appropriate user awareness. Rules governing the installation of software by users could also be established and implemented. This would reduce the residual risk score to ‘tolerable’.
Task Management
Ensuring all staff within your business are completing ISMS-related tasks, such as reading your mandatory policies, is essential to achieving and maintaining your ISO 27001 certification. One approach to this level of task management is via spreadsheets and emails, reminding staff when they need to complete tasks, but this can be a time-consuming and admin-intensive task for your information security officers.
Hicomply’s solution offers automated task management, allowing you to raise tasks that are automatically linked to assets, risks, policies and more, automatically notifying staff when a task is assigned to them. Learn more about automated ISMS task management.
Step Four: Build Your Policy And Procedure Library
The next step to achieve ISO 27001 certification is to document your policies and the processes that protect your data. Hicomply gives you all of the policies and procedures out of the box. We also enable your ISMS to function effectively as our software allows your business’s policies and procedures to be:
- Version controlled;
- Up to date;
- Accurate;
- Distributed;
- Read;
- Understood;
- Acted upon.
The number of policies required for ISO 27001 certification varies depending on the size of your business, your industry and the regulations or laws you must comply with.
Step Five: Create Your Statement Of Applicability (SoA)
ISO 27001 has 114 information security clauses in Annex A of the standard. Any organisation implementing an ISMS and attempting ISO 27001 certification must review its business activity against each clause to determine if it is relevant.
For relevant clauses, you must implement the necessary controls. Where you define any clauses as irrelevant or not applicable, you will need to justify this. In its simplest form, your business’s statement of applicability outlines this in a single point of reference. To create your SoA, ensure you include each clause, control ID, evidence of your decision to include or exclude each control in the scope of your ISMS, the process owner, and any further information such as risks mitigated. The SoA is typically a complex process but we have simplified the process providing a formatted SoA report at the end of our software driven workflow.
Step Six: Carry Out An Internal Audit
The last stage in this process is your internal audit. The internal audit is a key ISO requirement and is built into our software from day 1. An audit is key to ensuring your business’s ISMS meets the requirements for the ISO 27001 standard, and will put you in the best position for success when it comes to bringing in an external auditor. In addition, internal audits should be done regularly to ensure ongoing compliance. The standard does not require that you bring in a third party for your internal audit. Be sure to select auditors and conduct audits that ensure objectivity and the impartiality of the audit process. View the Hicomply ISO 27001 Internal Audit Checklist here.
How To Get ISO 27001 Certification Simply And Effectively
The above steps outline the process you and your business should follow when attempting ISO 27001 certification. By doing so, you’ll be in the best position to ace your external audit and achieve full ISO 27001 compliance. Looking to speed up the certification process? Get in touch with Hicomply to learn more about how we can automate and improve your business’s road to ISO 27001 implementation and certification.
Looking for further guidance on how to get ISO 27001 certification? Visit our ISO 27001 knowledge hub.
Ready to Take Control of Your Privacy Compliance?
See how Hicomply can accelerate your path to CAF compliance in a 15-minute demo.
