Smishing; a portmanteau of SMS (short messaging service; aka texting) and phishing; isn’t a new phenomenon. It’s a common tactic used by scammers; and the aim of the game is simple: to con unsuspecting victims into giving up key information; like their financial details or passwords.
Globally; smishing attempts are continuing to rise – data shows that fraudsters sent a staggering 87.8 billion spam texts in 2021; or 240 million a day.
Delivery companies are imitated most often. A survey by the Office for National Statistics revealed that more than half (54%) of respondents who received phishing messages said the sender had been posing as a delivery company; a third (32%) received messages apparently from their bank or building society; and a quarter (25%) from government services.
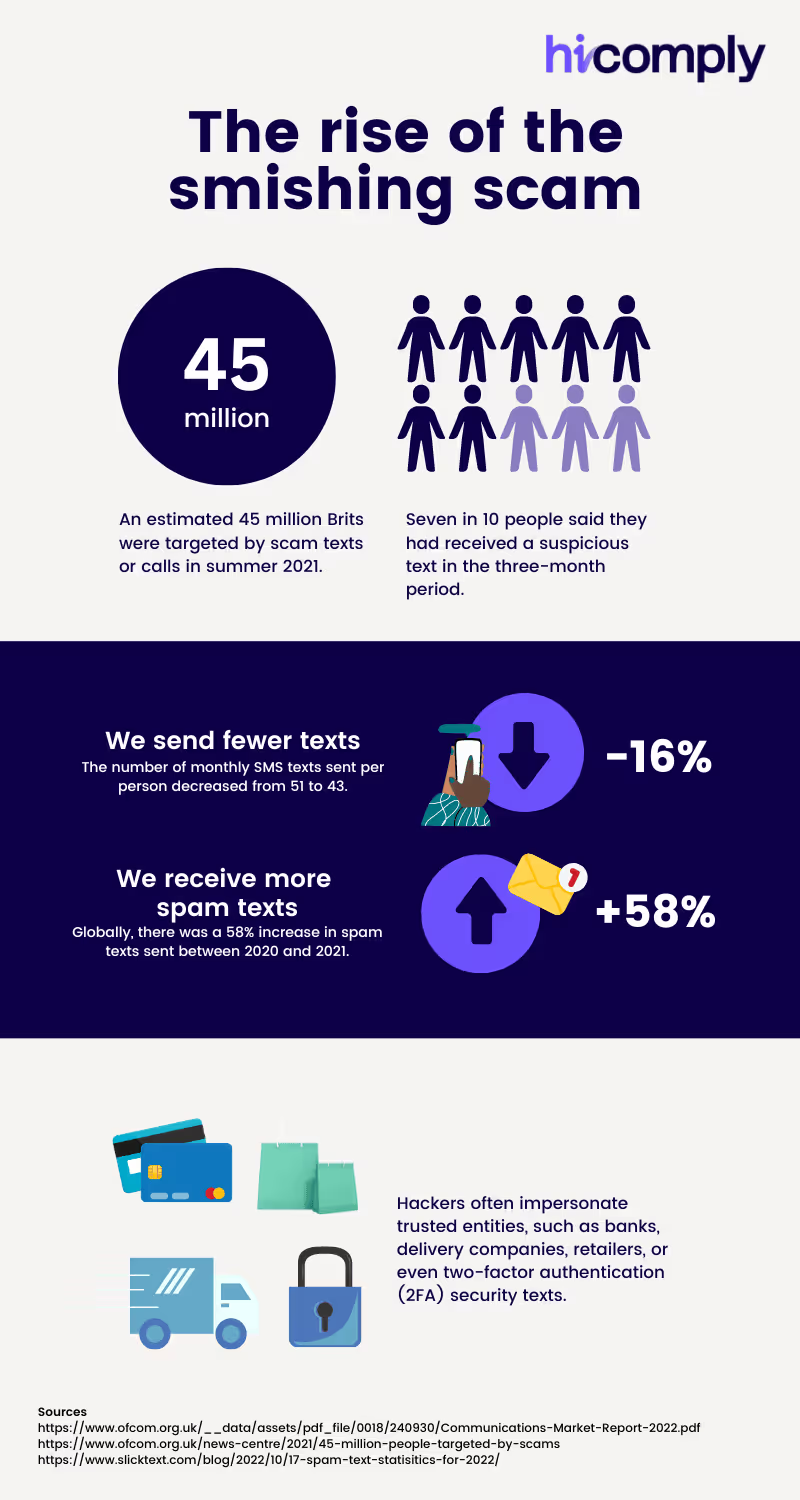
Brits are receiving more spam texts than ever
According to Ofcom; in summer 2021 an estimated 45 million Brits were targeted by scam texts or calls; and seven in 10 people said they had received a suspicious text.
Brits are sending fewer texts as applications like WhatsApp; Discord and Messenger see increased use – but we’re receiving more spam. The number of monthly SMS texts sent per person decreased by 16%; but globally; the number of spam texts received; including smishing attempts; increased by 58%.
When you receive a text you know is designed to steal your information; it can be tempting to send an angry response. But did you know that you could get into hot water for responding to spam messages?
Hackers are using sophisticated new tactics
Scammers often use a tactic called spoofing; which involves altering or completely changing the sender’s phone number to look like it’s coming from a different number entirely.
When this happens; there’s a chance that the number the scammer has imitated matches a real number belonging to somebody unrelated to the attempted scam. Your angry message or call may actually be directed at someone who wasn’t even involved.
Ed Bartlett; CEO at information security platform Hicomply; said: “There’s been a huge rise in scam texts since the start of the pandemic. Scammers can spoof numbers and imitate trusted authorities like your bank or your phone provider more easily than ever. The tech is getting cleverer and it’s becoming much harder for people to tell what’s legitimate and what isn’t.”
Clues that the text is a scam include:
- Misspelled words or bad grammar
- A link to a website that doesn't match the real brand's website
- A sense of urgency designed to make you panic and click the link
- Sent from an unknown phone number or a number not associated with the brand in question when searched online.
So what should you do if you receive a scam text?
Ed said: “The safest thing to do is report the text and block the sender’s number. Don’t click on any links and don’t provide personal or financial information. Whatever you do; don’t reply – you never know who you might be replying to!”
Most networks in the UK allow you to report scam texts by forwarding them to 7726. You can email screenshots or recordings of attempted scam texts or calls to the National Cyber Security Centre at [email protected].
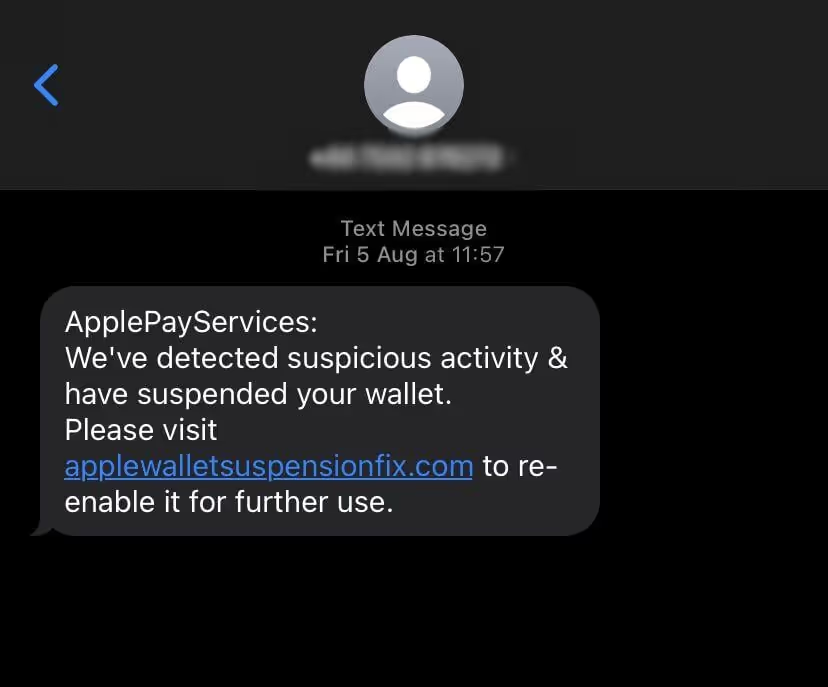
Phishing attempts on businesses are rising too
More broadly; phishing attacks and variations including voicemail-themed phishing attacks (vishing); browser-in-the-browser (BiTB) and adversary-in-the-middle (AiTM) increased by 47.2% in 2022; according to a report by Zscaler Threatlabz.
Attempts to scam businesses are also increasing. The Zscaler report also showed that the education industry experienced a huge 576% increase in phishing attempts; going from the eighth most targeted sector to the top targeted sector with over 30 million attacks; while finance and insurance saw an increase of 273%.
What is the cost of a successful phishing attack?
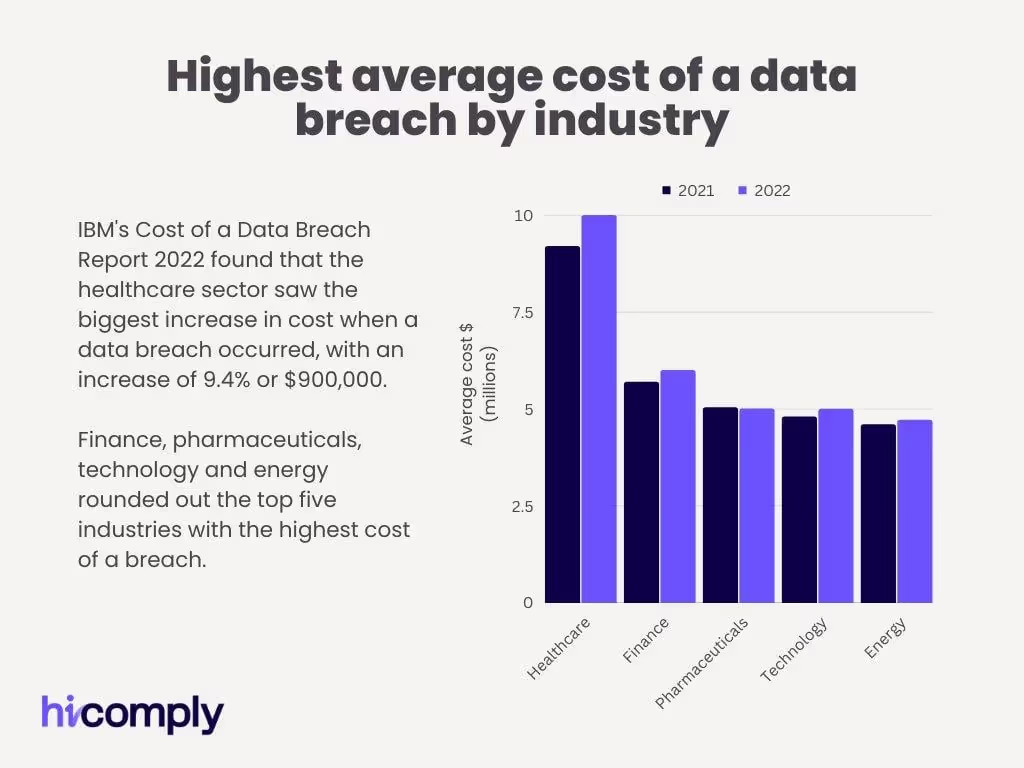
We all know successful data breaches can be costly to businesses; and IBM’s Cost of a Data Breach Report 2022 showed that the healthcare and financial industries in particular suffered significant losses as a consequence.
The average cost of a data breach in the healthcare industry went from USD $9.23million in 2021 to USD $10.10million in 2022; an increase of 9.4%. Meanwhile; the average cost for the financial industry went from USD $5.72million to USD $5.97million – an increase of 4.4%.
How can businesses fight back against phishing?
Hicomply CEO Ed Bartlett advises:
Educate your employees
Employees are your first line of defence against phishing; and many phishing attempts rely on human error. Educating your employees on red flags to look out for is key.
Use two-factor authentication:
Two-factor authentication; or 2FA; is an additional layer of security that requires users to provide two forms of identification before accessing sensitive information; making it harder for threat actors to gain access.
However; do not provide your 2FA codes to anyone; particularly if they are asking you to provide a code to confirm your identity. This may be a 2FA scam using social engineering.
Implement spam filters
Use spam filters to block phishing emails before they even reach your employees' inboxes; helping your business to reduce the risk of a costly human error.
Use encryption
Protect your business’s sensitive data by making it unreadable to anyone who does not have the proper decryption key.
Keep your software up to date
Ensure that your software has the latest security patches so that unauthorised access is more difficult.
Monitor your systems
Make sure you have a process to regularly check your systems for suspicious activity.
Implement an information security management system (ISMS)
An ISMS gives your business the tools to manage risks effectively. Ideally; your ISMS should be certified to ISO 27001; SOC 2 or equivalent.
Sources
- Robokiller: 2022 Phone Scam Report
- Ofcom: 45 million people targeted by scam calls and texts this summer
- Ofcom: Communications Market Report 2022
- Office for National Statistics: Phishing attacks - Who is most at risk?
- IBM: Cost of a Data Breach 2022 Report
- Zscaler Threatlabz: 2023 Phishing Report





.svg)


%20(1).png)


