Task management is an essential part of building and maintaining an effective information security management system (ISMS).
Tasks can include everything from running risk assessments to assigning required policies and documents for employee reading; and while many tasks involve only a select team members or department heads; some; such as required reading; can involve everyone in your organisation.
In this article; Hicomply’s qualified digital ISMS experts give their top tips for managing tasks in your ISMS.
Log key ISMS meeting actions as tasks
After every ISMS meeting; you should log any actions as tasks in your ISMS. This ensures that the task owner is assigned and the action is effectively managed; so it can be monitored and you can ensure the action is completed before the following meeting. We recommend not creating standalone ISMS meetings and simply adding as an agenda item to existing standing meetings to keep your operation lean.
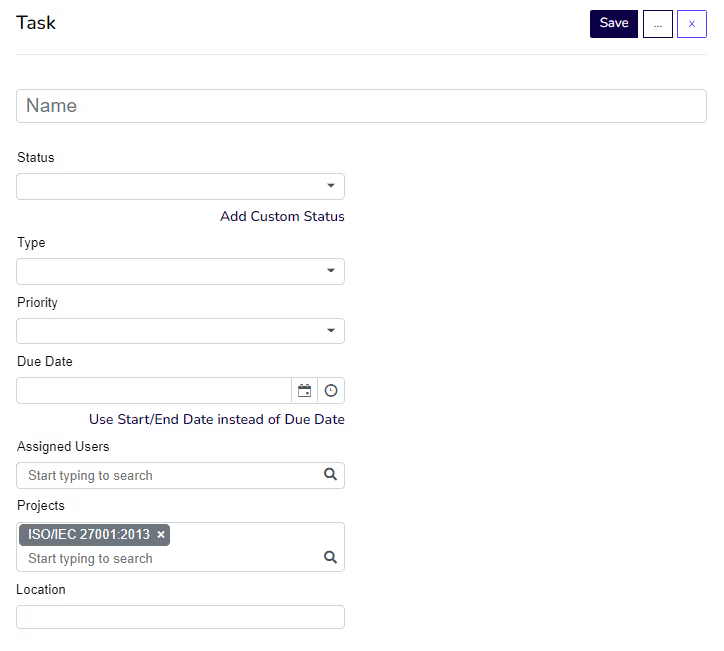
Within the Hicomply platform; creating tasks is simple. To create a standalone task; select ‘tasks’ in the navigation bar; then select ‘create’. From there; you will be able to name the task; add its status; type; priority and due date. You can also assign users; assign the task to a project; and add a location.
Create annual recurring tasks
To maintain the maturity of your ISMS; we suggest creating annual recurring tasks. Often; these tasks are an important part of maintaining compliance with the standard you’re looking to achieve.
Using Hicomply; you can create recurring tasks by following the task creation process outlined previously; and choosing how often the task recurs under the ‘repeat’ field. In the drop down menu; you’ll see the following options:
- Never
- Daily
- Weekly
- Monthly
- Annually.
Your tasks can also be linked to documents and project management tools like Trello and Asana.
Examples of recurring tasks include:
Access review
An access review involves ensuring your access policy is up-to-date; and addressing all access rights regarding your company's data; applications; and infrastructure. This should involve monitoring which access rights are authorised and the level of access each user or user group has.
Supplier review
A supplier review involves the evaluation of your organisation’s suppliers and their information security practices to ensure they align with your organisation’s requirements and security posture. ISO 27001; for example; requires organisations to monitor and review their supplier services on a continuous basis to remain compliant.
Policy and procedure review
Your organisation’s policies and procedures form the foundation of the ways in which you protect your customers’ data and reduce the risk of any reputational or financial loss. Because of this; you should review them at least once a year to ensure they are up to date and still relevant to your organisation.
Risk assessment
The risk landscape within any organisation is ever-changing. Having an up-to-date risk assessment is crucial to ensuring you’re aware of and working to treat risks to the security of your data. A year on from your original risk assessment; with a more mature ISMS and a better idea of organisational risk; you might decide to change your approach to addressing certain risks or switch to a different method of treatment entirely.
Log audit findings and non-conformances
When you receive your internal or external audit report; you should log all findings and non-conformances as tasks within your ISMS. Doing so means you can effectively manage your tasks; delegate responsibilities as required and prove that you have taken action to remedy any non-conformances.
Logging any findings and non-conformances in your ISMS is good practice and can be used as evidence for any surveillance audits needed to maintain your certification or standard.
Final thought
A strong approach to task management is not only crucial for an effective ISMS; it also makes maintaining and maturing your ISMS easier. The actions your organisation takes to resolve key tasks can also be used as evidence to maintain your standards; proving to both customers and prospects that you take information security seriously.





.svg)





