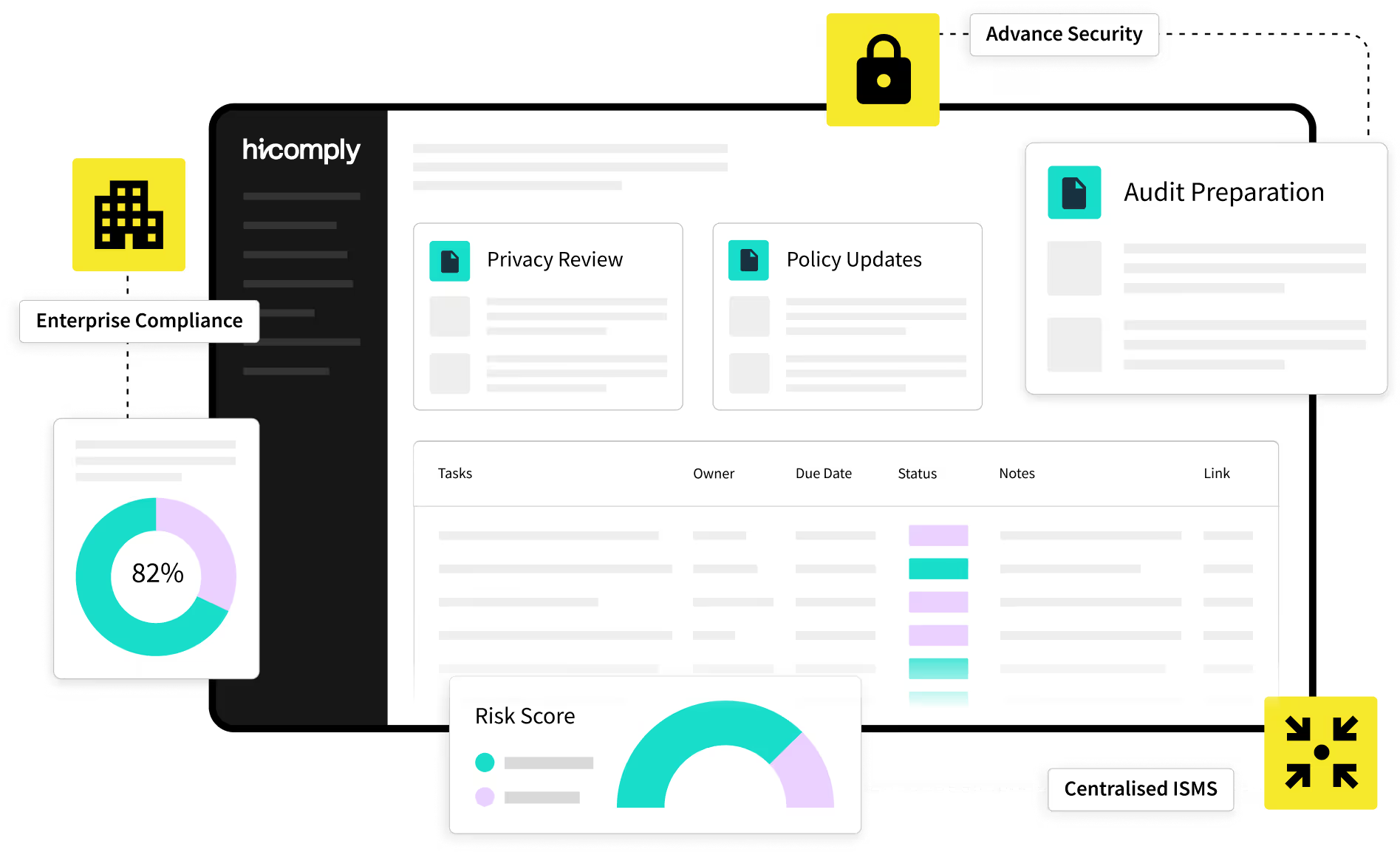
Enterprise Compliance That
Makes You Unstoppable
Skip the complexity and crush compliance at scale. Hicomply's ISMS powerhouse automates your frameworks, eliminates manual work, and keeps your enterprise audit-ready 24/7.










Trusted by Compliance, IT, and InfoSec Teams in Organisations Worldwide.




































Your All-in-One ISMS Powerhouse
No hacks, just Hicomply. Get the tools that make enterprise compliance look easy.
Skip the Grind, Crush Enterprise Compliance
Get everything you need to make compliance a competitive advantage.

Automation at Scale
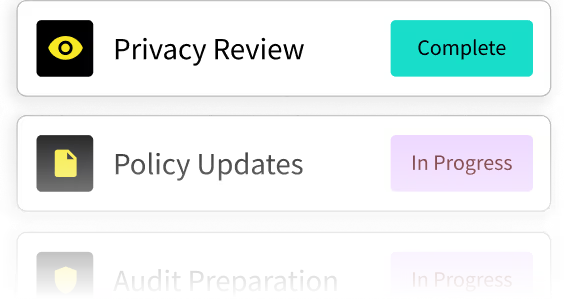
Transform your workflows with smart automation, policy updates, and reminders for effortless compliance.

Real-Time Dashboards
Get instant visibility into your compliance status and tackle risks with real-time intelligence.


Seamless Integrations
Connect smoothly with tools like Microsoft 365, Okta, and more for seamless operations.
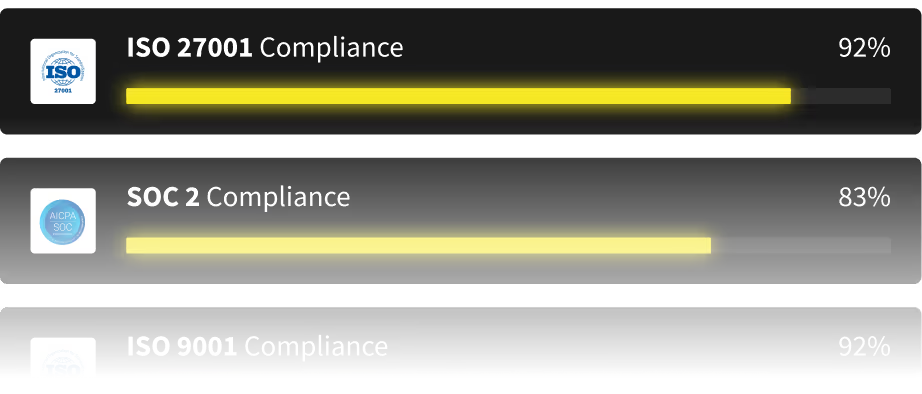
Handle ISO 27001, SOC 2, and more from one powerful platform asdasd

Advanced Security
Safeguard your organisation's sensitive data with enterprise-grade security and controls

Audit-Ready Reporting
Create detailed, audit-ready reports that meet compliance standards without the hassle.
See Why Enterprises Choose Hicomply

“The Hicomply platform makes the process of auditing easier and reduces the need for extensive auditing meetings, saving us time and resource”
Tanveer Hafeez
Head of IT and Information Security

Ready to Feel in Total Control of Compliance?
Join enterprises who've transformed their compliance from chaos to confidence.